Secure Archive REST API
A security-hardened JSON REST-style application programmer's interface that adds Authentication and Authorization to Precisely®1 EngageOne™1 Vault.
- Built in the highly-respected Rust programming language to deliver reliable and efficient software that is vulnerability resistant
- Runs on Linux or Windows. No need for SQL, Java, nor Tomcat
- Implementing the Rendering Engine
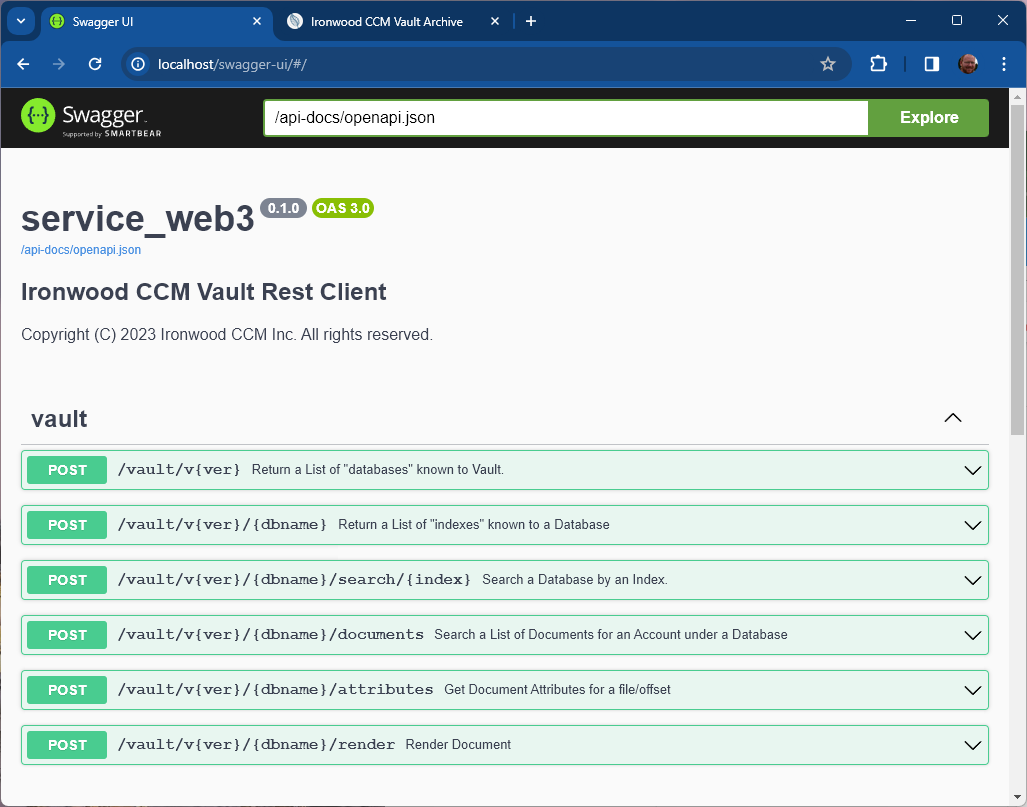
Wire API per the Programming Reference Guide - Ergonomic to Software Developers: Intuitive methods, requests, and responses for rapid software development
- Includes OpenAPI documentation with an embedded Swagger-Ui front-end
- Single Sign-On Authorization via OAuth2. Connects to Okta, ForgeRock, Azure AD, Entra ID, and many more
- Access Control using OpenID Connect
claims to limit access to each Vault Database - Server performs Back-channel OAuth2 and OpenID Connect Token Validation to prevent forged tokens
- Uses Okta authentication patterns
- Support committment for zero High- and Medium-severity OWASP vulnerabilities
- Three Security Configuration Options: None (not recommended), OAuth2 Required, or OAuth2 Role-Based Access Control
- Easily reverse-proxied behind IIS or NGinx for SSL, load-balancing, fault tolerance
- Memory Safe, Multi-threaded, high performance and scalability, very low system requirements
- Configuration in .toml format; Overrides via Environment Variables for Containerization
- Strongly-typed payload checking to mitigate strengthen Buffer-overflow protection in Vault (C++ based) components
- Data-Leakage protection ~ Error messages are redacted to an Incident ID rather than passing detailed data back to callers
Authentication
Authentication can be configured to business requirements.
# Require OAuth for vault APIs
# Enable OAuth-Based Security.
# WARNING: setting this value to false gives unrestricted access to Archive documents.
oauth-enabled = true
# Role-Based Access Controls aka OpenID Connect, enables 0 or more "permissions" claims per user
oauth-rbac = true
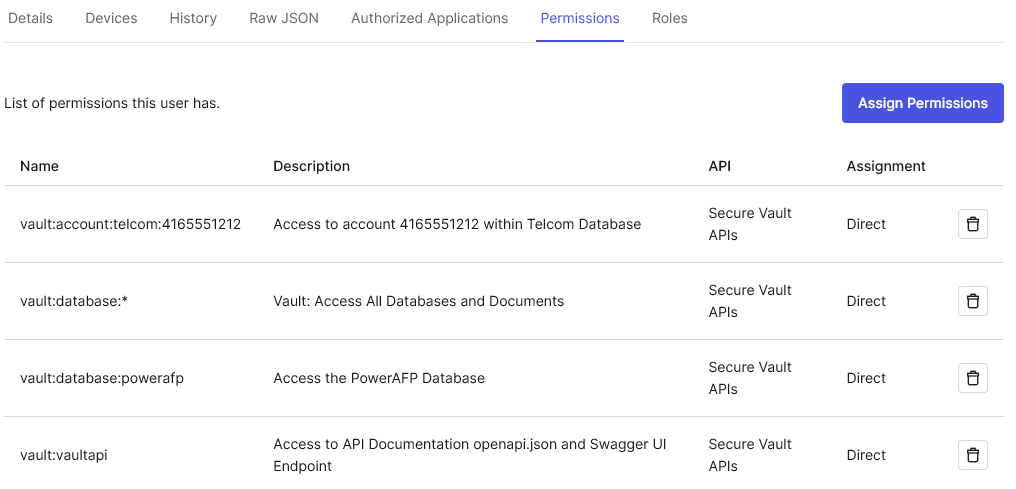
# "vault:vaultapi" access to SwaggerUI + OpenAPI.json -- grants no archived document access
# "vault:account:telcom:12345" access only to account 12345 in database "telcom". [Experimental]
# "vault:database:soandso" access to all documents in the "soandso" database
# "vault:database:*" access to all documents in all databases, e.g. everything in vault
# Allow access to SwaggerUI and OpenAPI.json without requiring the vault:vaultapi claim.
insecure-enabled = false
# If a user is not authenticated, redirect to this endpoint for a Login.
# This endpoint should be reachable by HTTPS with suffix /.well-known/jwks.json
oauth-domain = "dev-3xamp1e.us.auth0.com"
# Audience value for aud= portion of request aka API Identifier.
oauth-audience = "https://ironwoodccm.ca/api"
# Todo on OAuth provider: Allow the endpoint that this service is exposed as.